Disclaimer: Please make sure you always have a backup of your settings/configs before you make any changes so that you can easily roll back the changes you try to make. Likewise, you are using these directions of your own volition and I am not responsible for helping you get things working again if these don’t work perfectly with your setup.
So you want to setup some security related networks on your Unifi Gateway but you still want to be able to Chromecast or AirPlay to a device on your IoT network but block everything else? Well here are some helpful steps on how to accomplish this.
The first thing that you need to do if you want to have Chromecast or AirPlay work between networks is browse over to the settings area. Once you are in the settings click on Networks. On this page, there is a setting under Global Network Settings for Multicast DNS. Make sure that this is enabled and any network that you want to cast to/from is in the list.
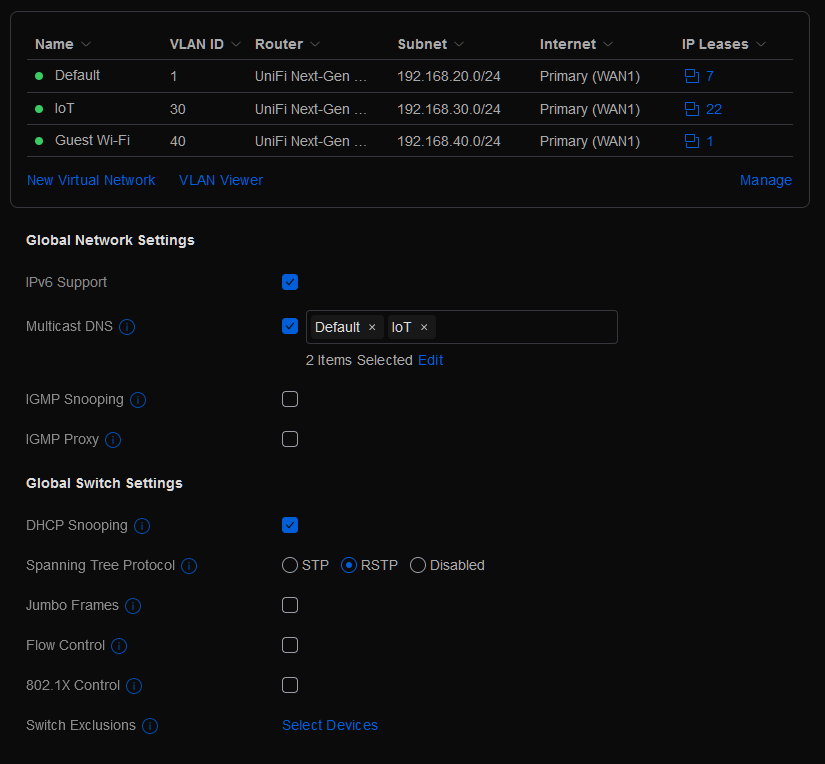
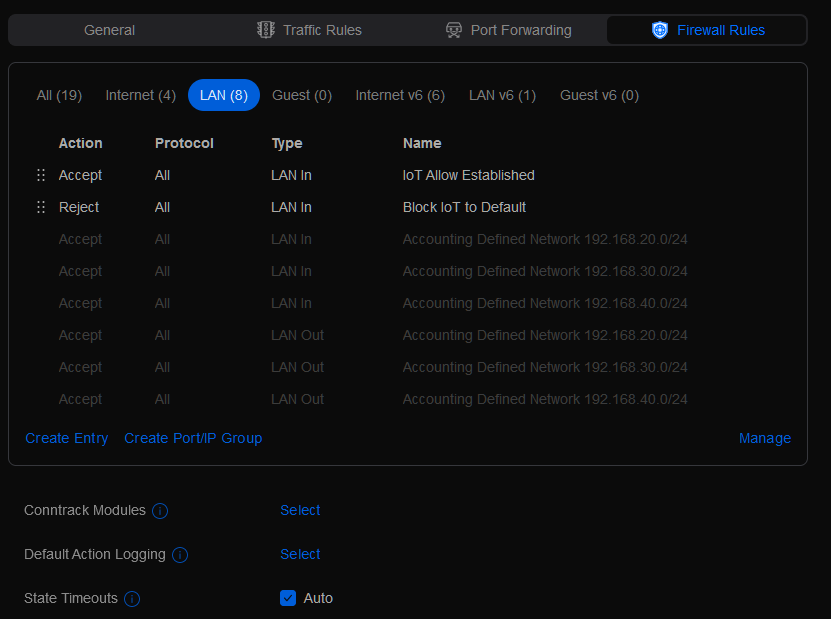
Once that is gone, then go to the Security section. By default all traffic coming into the LAN on your network is allowed to get to anything it wants to. You’ll want two main rules configured if not more. One that will block the IoT network from accessing the main network. The other, will allow ‘established’ connections to exists from the IoT network back to the main network.
Below is the order of the two rules in question.
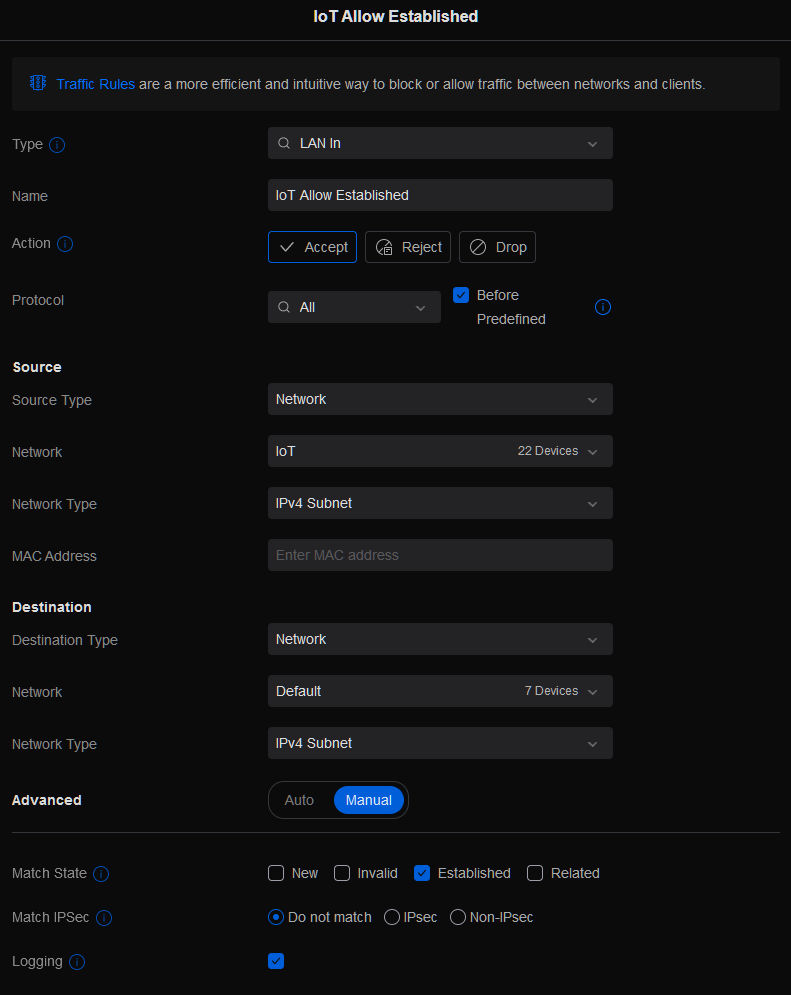
The ‘IoT Allow Established’ rule looks like this:
The ‘Block IoT to Default’ looks like this:
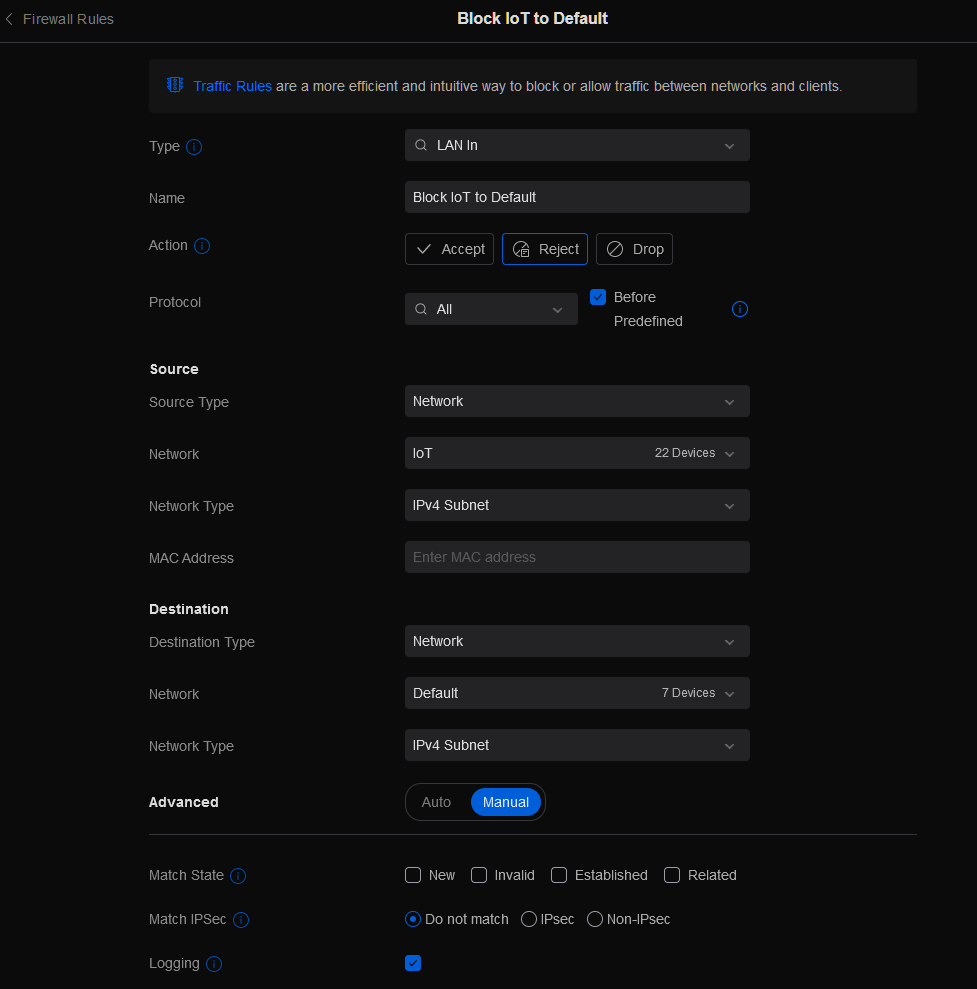
The combination of these rules in this order works like this. Anything initiated from the default network to the IoT network, is viewed as an ‘Established’ state and so the first rule allows traffic that was already created to function. The second rule, blocks all traffic from the IoT network to the Default network. Because we listed this AFTER the rule that covers established connections.
This should resolve any issues that you have getting this type of configuration to work. I did some testing among multiple systems on the IoT network in my environment trying to get to systems on the default network and was unable to.
